Become an IAM Policy Master
Become an IAM Policy Master (AWS re:Invent 2018)
1. Recap of IAM policy language
2. Policy types and how they work together
3. Deep dive on policy with specific use cases.
# Set permission guardrails across accounts.
# Control creation of resources to specific regions.
# Enable developers to create roles safely.
# Use tags to scale permissions management.
What are IAM policies?
Policies provide authorization to AWS services and resources.Two parts:
# Specification: Defining access policies. (User's job, User decide who should have access to what, and you do that by writing policy)# Enforcement: Evaluating policies. (AWS's job, AWS evaluate every aws requests that comes in by 'can this person', 'call this action', 'on this resource', 'on this time / day', 'from this source' etc..)
When you define access policies, You specify which IAM principals are allowed to perform which actions on specific AWS resources and under which conditions.
IAM enforces this access by evaluating the AWS request and the policies you defined and returns either yes or no answer.
IAM policy structure (PARC model)
{"Statement": [{
"Effect":"effect",
"Principal":"principal",
"Action":"action",
"Resource":"arn",
"Condition":{
"condition":{
"key":"value"
}
}
}]
}
Principal - The entity that is allowed or denied sccess
"Principal":"AWS":"arn:aws:iam::123456789012:user/username"
Action - Type of access that is allowed or denied access
"Action":"s3:GetObject"
Resource - The Amazon resource(s) the action will act on
"Resource":"arn:aws:sqs:us-west-2:12345678012:queue1"
Condition - The condition under the access defined is valid
"StringEqualsIfExists":{"aws:ReuestTag/project":["Pickles"]}
IAM policy evaluation
1. The decision starts at Deny2. Evaluate all applicable policies
3. Is there an explicit Deny?
Yes --> Final decision = "Deny" (explicit Deny)
No --> Is there an Allow?
Yes --> Final decision = "Allow"
No --> Final decision = "Deny" (default Deny)
Context and policies - a new way to think about evaluation
| Context of your Request ---> | An Alien | <--- Your Defined Policies |
| (The unique components of each AWS request) |
|
|
(The policies you define on identities, resources, and organizations) |
V
|
||
| Allowed / Denied |
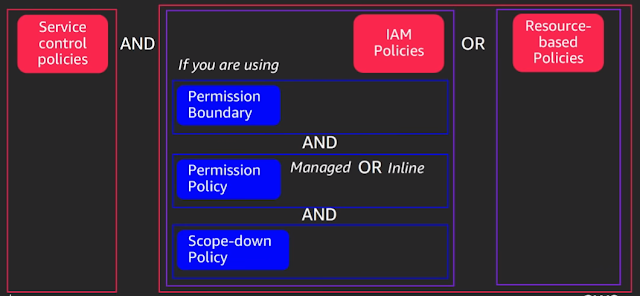
Policy types and core use cases (All use the same policy language)
| AWS Organizations | Guardrails to disable service access on the principals in the account |
| Service control policies (SCPs) | |
| AWS Identity and Access Management (IAM) | Grand granular permissions on IAM principals (users and roles) and control the maximum permissions they can set |
| As Permission Policies and Permission Boundaries | |
| AWS Security Token Service (AWS STS) | Reduce generally shared permissions further |
| Scoped-down policies | |
| Specific AWS services | Cross-account access and to control access from the resource |
| Resource-based policies | |
| VPC Endpoints | Control access to the service with a VPC endpoint |
| Endpoint Policies |

Comments
Post a Comment